Streamlining Threat Detection and Response with ReversingLabs and Microsoft Sentinel
Introduction
In today’s rapidly evolving threat landscape, Security Operations Centers (SOCs) face the daunting challenge of efficiently detecting, analyzing, and responding to a myriad of cyber threats. The integration of advanced tools is no longer a luxury but a necessity. One such powerful integration is between ReversingLabs and Microsoft Sentinel, a cloud-native Security Information and Event Management (SIEM) solution. This partnership equips SOCs with advanced threat intelligence and file enrichment capabilities, significantly enhancing their operational efficiency. In this article, we will delve into how these integrations bolster security operations and streamline incident response.
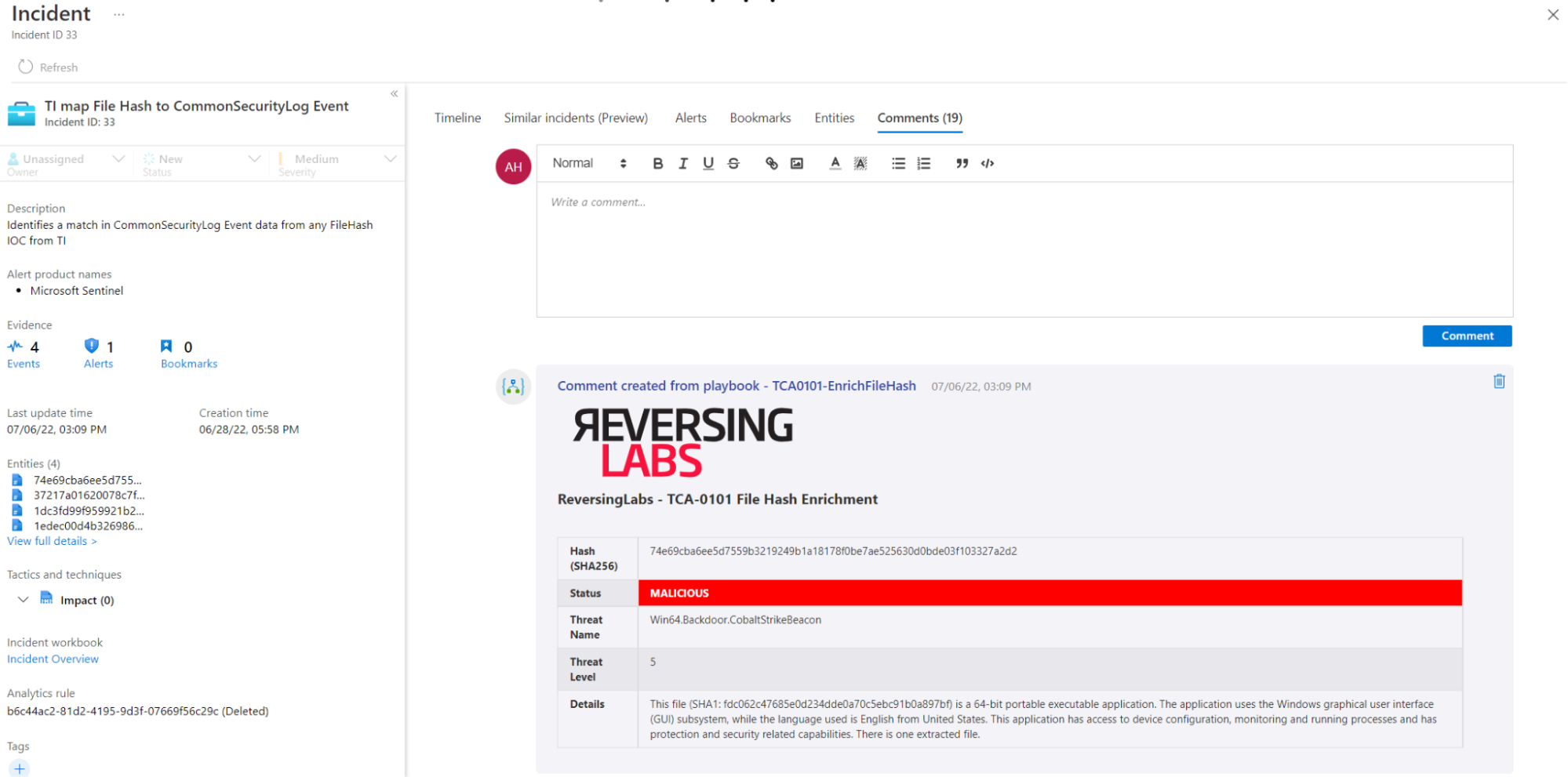
Microsoft Sentinel Incident Handling Page with ReversingLabs Enrichment
ReversingLabs and Microsoft Sentinel: A Powerful Partnership
ReversingLabs is a proud member of the Microsoft Intelligent Security Association (MISA), ensuring that their integrations undergo rigorous review by Microsoft Engineers for optimal service integration. This collaboration is pivotal in providing SOCs with comprehensive threat intelligence and file reputation services, ultimately reducing triage time and analyst fatigue. By delivering actionable insights and automating key processes, ReversingLabs enhances the capabilities of Microsoft Sentinel, making it an indispensable tool for modern security teams.
Key Offerings in the Azure Marketplace
ReversingLabs offers a suite of products in the Azure Marketplace designed to enhance threat intelligence and incident response capabilities:
-
ReversingLabs Content Pack for Microsoft Sentinel: This comprehensive suite includes sample playbooks that automatically enrich incidents with file hash reputation information from ReversingLabs’ Spectra Intelligence and Spectra Analyze platforms. It also features a workbook that provides insights into threat intelligence feed quality, incident metrics, and operational efficiency.
-
ReversingLabs Scanner for Microsoft Defender: This tool integrates file-based threat intelligence directly into the Microsoft Defender incident interface. By leveraging the Microsoft Defender Streaming API, it provides insights into file characteristics, including malware classification and MITRE ATT&CK tactics. With access to ReversingLabs’ extensive database of over 40 billion searchable samples and 385 billion file hashes, analysts can swiftly identify and respond to potential threats.
-
ReversingLabs Enrichment APIs for Sentinel: These APIs empower security teams to enhance malware detection capabilities by integrating advanced file reputation and hash analysis into their Sentinel workflows. This integration allows SOC teams to classify files as good, bad, or suspicious quickly, significantly reducing incident triage and response times.
- ReversingLabs – Early Detection of Ransomware for Sentinel: This solution provides a powerful mechanism for detecting ransomware threats within networks. By integrating curated indicators into the Sentinel TAXII data connector, organizations can proactively identify and mitigate ransomware threats at various stages of the attack lifecycle.
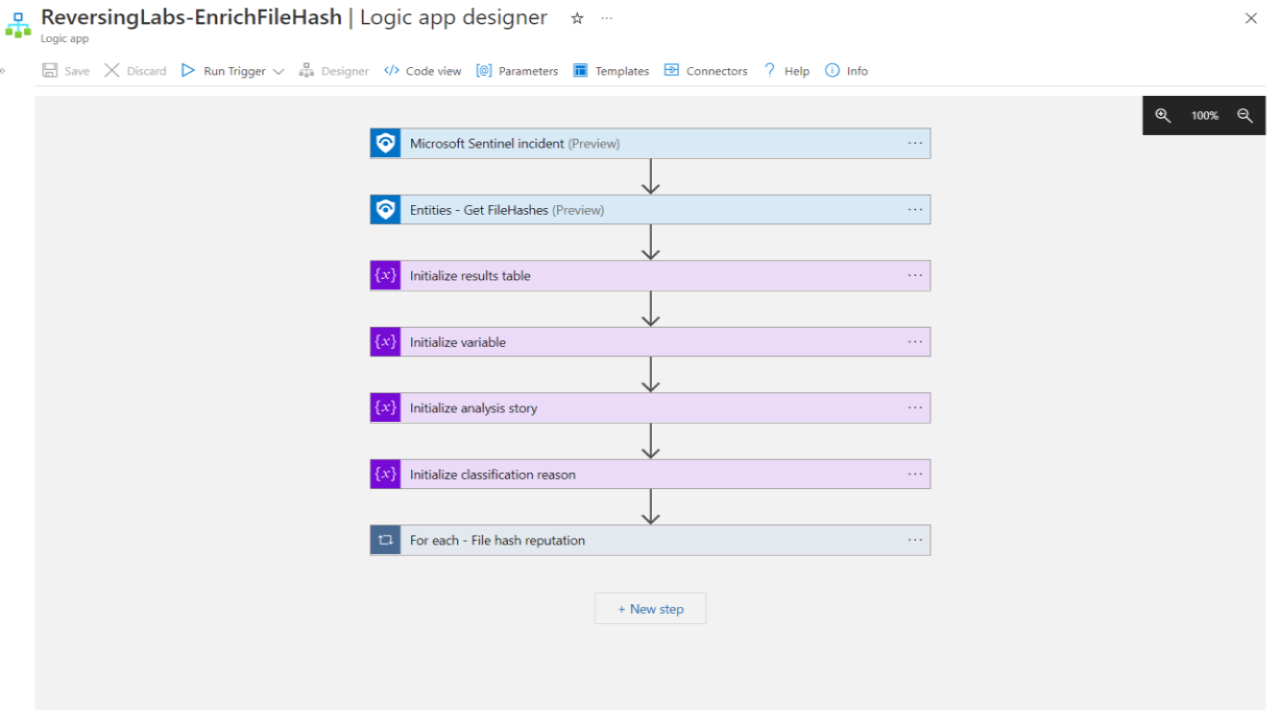
An automatically formatted enrichment security incident
Practical Applications
Investigating Security Incidents
The integration of ReversingLabs’ threat intelligence within Microsoft Sentinel allows SOC analysts to investigate security incidents with greater efficacy. By providing deeper visibility and advanced context for Indicators of Compromise (IOCs), analysts can better understand the nature and scope of threats. The ReversingLabs file reputation API can automatically triage alerts generated by endpoint protection solutions like Microsoft Defender, examining associated files and enriching incident reports in a consistent format. This automation can save SOC teams hundreds of hours of manual investigation.
Automating Incident Response
The ReversingLabs Content Pack for Microsoft Sentinel includes sample playbooks designed to automate incident enrichment with file hash reputation information. This automation accelerates incident response and enhances SOC performance by minimizing manual analysis efforts.
For instance, once a file is classified as goodware, malware, or suspicious, the playbook can trigger a series of automated responses. Goodware can be released from email quarantine, while an infected endpoint can be isolated from the network and scheduled for reimaging. In cases of suspicious files, they may be tagged for further investigation, such as being sent to a ReversingLabs Sandbox. Such automation not only saves significant operator time but also ensures a more consistent and effective incident response.
Conclusion
The integration of ReversingLabs with Microsoft Sentinel presents SOCs with a formidable combination of threat intelligence and file enrichment capabilities. By leveraging these integrations, organizations can enhance their security operations, reduce triage time, and respond to threats more efficiently.
As the threat landscape continues to evolve, it is crucial for security teams to stay ahead of potential risks. Ready to enhance your security operations with cutting-edge threat intelligence and file enrichment? Discover how ReversingLabs’ integration with Microsoft Sentinel can transform your SOC’s efficiency and effectiveness.
Explore the integration today and empower your team to quickly detect, analyze, and respond to threats. Visit our ReversingLabs Integration with Microsoft Sentinel page to learn more and get started!
This is a Security Bloggers Network syndicated blog from ReversingLabs Blog authored by Stuart Phillips. Read the original post at: Streamlining Threat Detection and Response with Unified Solutions
